PicoCTF 2024 Web Exploitation Challenges
بِسْمِ اللهِ الرَّحْمٰنِ الرَّحِيْمِ

Hello and welcome again, I’m Ahmed Reda (0xHunterr) and this is a walkthrough for most of the Live Web Exploitation Challenges of PicoCTF 2024, let’s go

Trickster


challenge website
the challenge is basically about an app with a file upload function for the.png files, Most file upload vulnerability challenges can be solved in 2 Chapters
the first is to try to find a way to bypass the validation to upload a shell
is to try to traverse through the server to access your uploaded shell So let’s start with
Chapter 1: Bypassing file upload
the first thing I did was to test it, I tried to upload a random file (not PNG) to see the behavior and inspect the request trying to figure out if the validation is a Client-side or Server-side

and it rejects it saying doesn’t contain the “.png”, so it’s predictable to be rejected but the literal line of “.png” in the error message gave me the hint that the server validated the file by checking hard-coded .png in the file name
so I have uploaded a file with the name test.png.php and some PNG magic bytes and it passed successfully!
The content of the file was a simple PHP shell:
Chapter 2: Traversing and accessing our file
to access the shell I tried to fuzz and make directory enumeration
and as usual in challenges of this type, I found a directory called uploads but with 403 access denied page

I noticed the web server is Apache 2.4.56 so I started to search for any CVEs for it and I found CVE-2023–25690 and it’s about Access Control

but we didn’t need to exploit it, once I tried to access the file directly /uploads/test.png.php it worked and showed the command output

the output of
so I started to search for the flag, it usually in a file called flag.txt or pico for example but I didn’t ding any of them so searched the whole system for any .txt file using the following command
find /home -name *.txt

the output of _find_ /home -name *.txt
We can notice a strange file called G4ZTCOJYMJSDS.txt so I tried to open it
cat /var/www/html/G4ZTCOJYMJSDS.txt

and here we go picoCTF{c3rt!fi3d_Xp3rt_tr1ckst3r_73198bd9}
No Sql Injection
The Challenge
challenge website
the first thing that comes to mind when I see a login page is to try the SQL injection "OR "1"="1"

but no, not this time, when I viewed the source code I found that it’s a Node and React app and it’s using Mongoo database which is a NoSQL database

database connection code
so instead I tried the Nosql Injection and started to look at the source code for the login page
so from the source code, this basic payload will do the job { "$gt": ""}
and it worked and I logged in to an Admin page

But it’s weird cuz it has no functionality it’s just static, so I tried to inspect for any secrets but also nothing interesting

back to the login page and Nosql injection when u try it from Burp or any proxy u will get some info in the response, the app is just filtring the info from the client side here

when u try to log in with these creds u will get the same admin page but the token of the user looks interesting since it has == at the end of it so tried to Base46 decoding it and.. here we go

the flag: picoCTF{jBhD2y7XoNzPv_1YxS9Ew5qL0uI6pasql_injection_a2e0d9ef}
IntroToBurp

It showed me a register page, so I registered

and then got redirected to a 2fa page that needed OTP, the view of the page just gave me the vibe that it is not even working, so I decided to play with the request and see if I can bypass it


The OTP submit request

the first thing I tried was to delete the OTP parameter, and it worked
it doesn’t validate or check anything the flag: picoCTF{#0TP_Bypvss_SuCc3$S_c94b61ac}
WebDecode

challenge website
challenges like these is just about inspecting and finding a secret hidden in the pages somewhere
so I opened the inspector and started searching for anything interesting and found in the about.html page

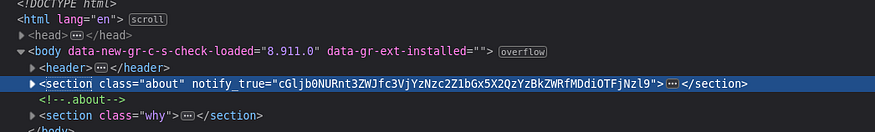
notify_true=”cGljb0NURnt3ZWJfc3VjYzNzc2Z1bGx5X2QzYzBkZWRfMDdiOTFjNzl9"
it seems to be encoded so i tried to decode it as base64

here we go: picoCTF{web_succ3ssfully_d3c0ded_07b91c79}
Bookmarklet
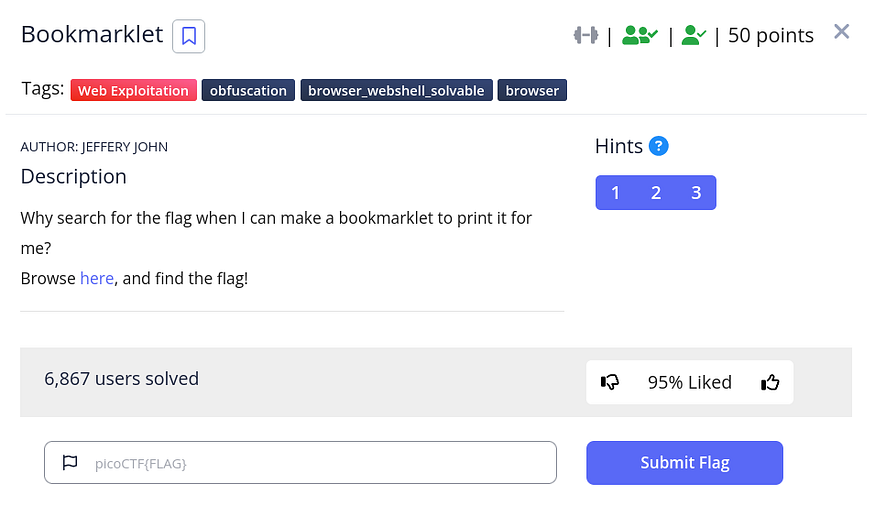
challenge website
it shows the following js code:
that seems to be decrypting the flag so I just ran it in the debugger
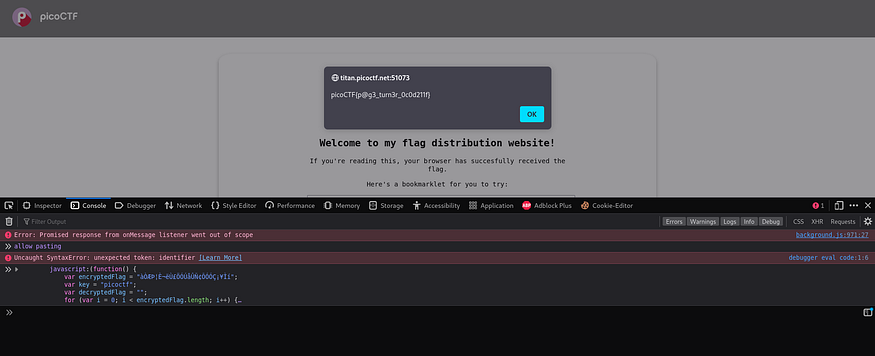
it alerted the flag: picoCTF{p@g3_turn3r_0c0d211f}
Unminify


challenge website
I started searching using the sources tab for anything interesting and enabled the pretty option in it

and I found it as clear as it can be picoCTF{pr3tty_c0d3_d9c45a0b}
that’s it for this CTF see you in the future Inshaa Allah, Pray for me 🙏
If you have any questions, You can reach me through my social accounts: Twitter(X) | Linkedin | Github | Facebook  “Hide the Pain”
“Hide the Pain”
Last updated