Intigriti 1337Up 2024-CTF OSINT Challenges
بسم الله الرحمن الرحيم والصلاه والسلام على سيدنا محمد Hey there, this is SirReda (AKA 0xHunterr), and this is a walkthrough for the OSINT challenges I solved in Intigriti 1337 Up 2024-CTF

content:
Trackdown
Trackdown2
No Comment
Trackdown:

We can see in the provided image a huge building with the title “Trang Tien Plaza” heading to Google Maps and hitting the street view to locate the exact angel
note that the question here is from where the photograph was taken? not what is the photo is? and also note that there is two or more entrance for the building but our target is the one with GUCCI
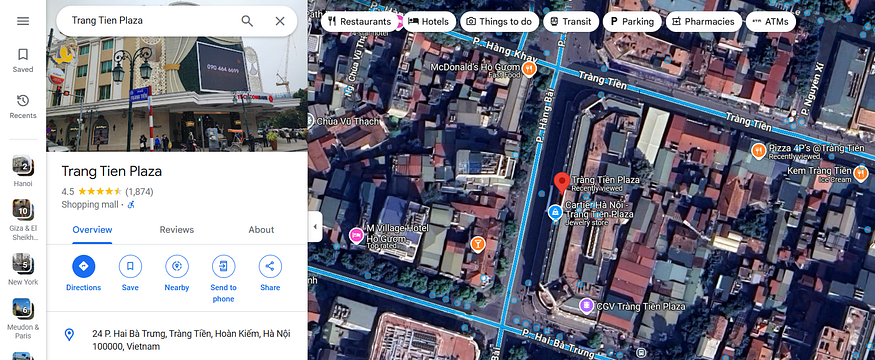

after digging around we got the place
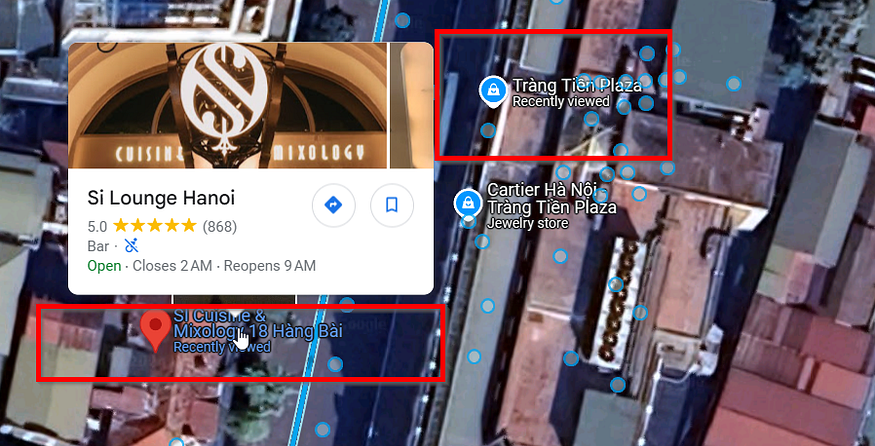
simulating the angel of our image we could see a restaurant but I couldn’t find any tables perhaps cuz the image was a night and our view is morning so there are some changes
anyway trying that restaurant and it worked
flag: INTIGRITI{Si_Lounge_Hanoi}
Trackdown2:

Trying to reverse the image to get initial clues
not the best results but fine
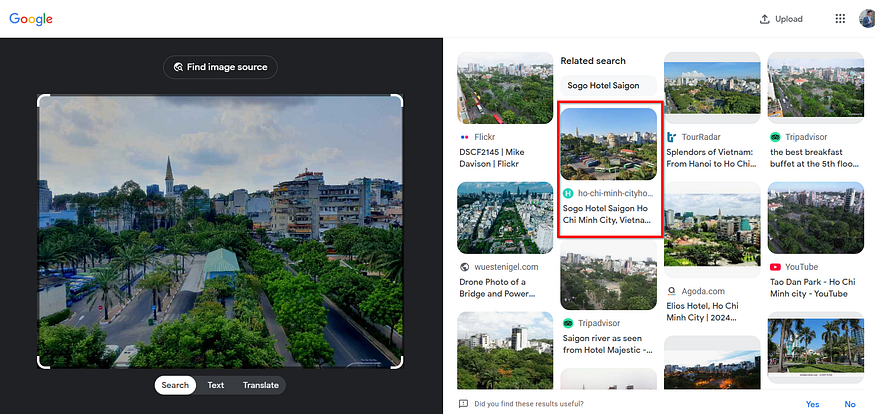
trying to be specific in our search we can see that high tower in the photo I can use it
got the name of the bulding and the City
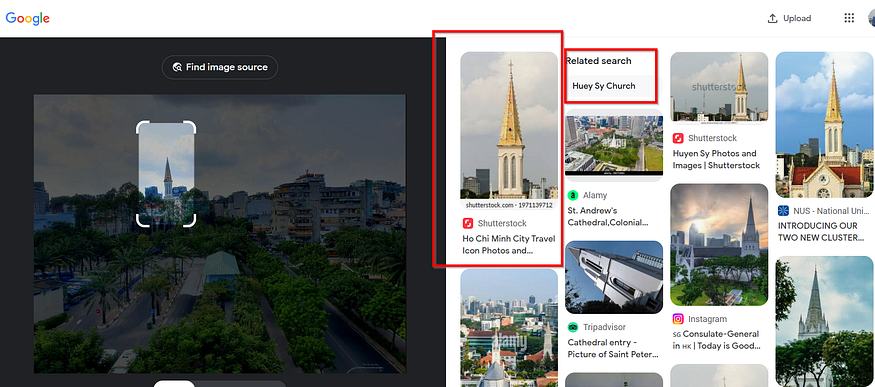
searching for clues in the provided image, zooming in to the right side I could see a lot of titles and text that will be helpful


let’s collect the sources we have now, we search for the little hanoi egg coffee next to the simple cafe and A25 Hotel and a Bus station or something
Searching Google Maps for little hanoi egg coffee
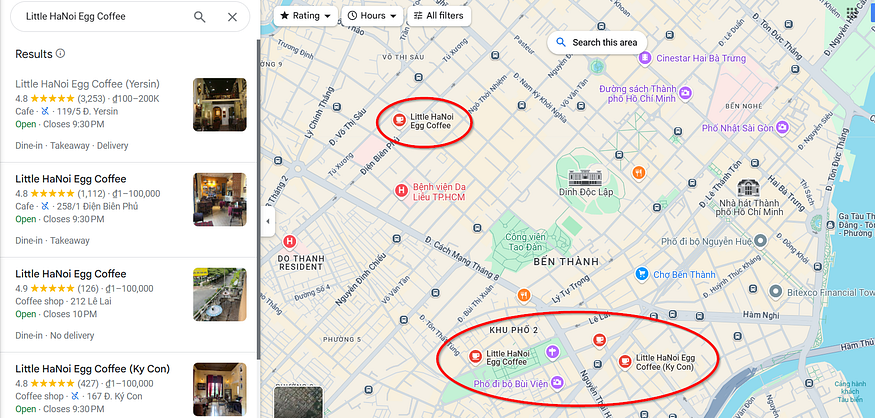
after checking them by zooming + satellite mode, the left one is our target
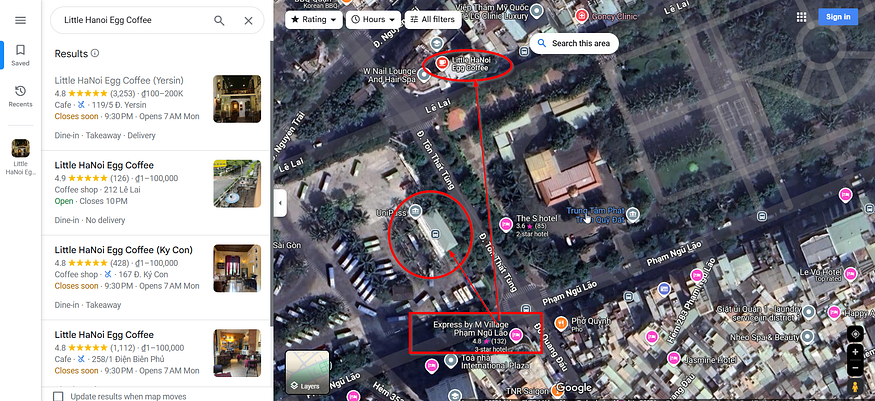
this place is the most reasonable one
flag: INTIGRITI{Express_by_M_Village}
No Comment

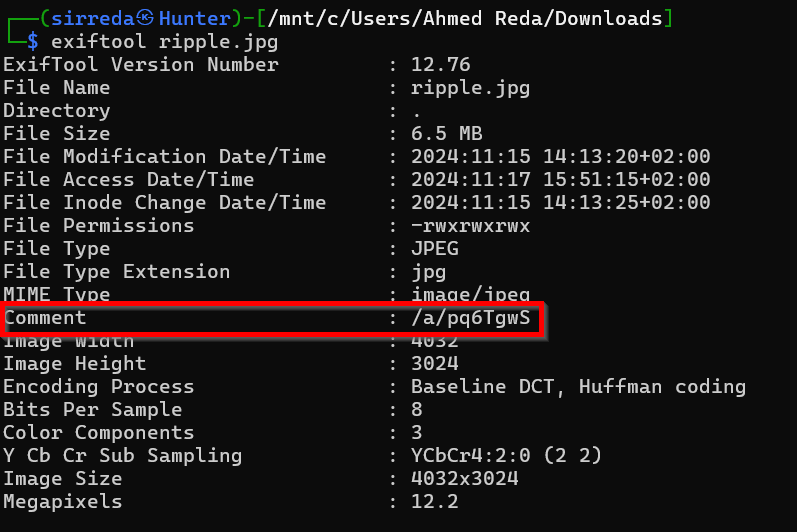
the name of the challenge gives us the vibe of metadata or stegno more than reversing the image, examining the EXIF data:
encoding didn’t work here so I started to think a different way
craving help from GPT
validating its response I got this on Reddit, going to the link imgur.com/a/pq6TgwS
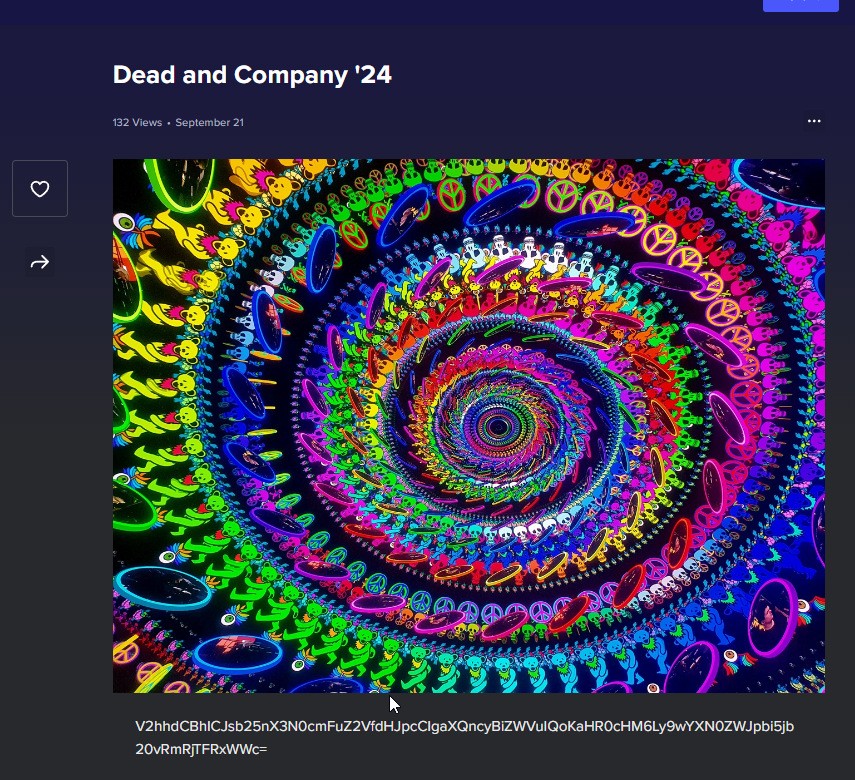
decoding it with Base64
What a "long_strange_trip" it's been!
https://pastebin.com/FdcLTqYg
going to the Pastebin link and found a protected paste with a password after revising my approach for any missing pieces, there is nothing missed
but the pass is in front of us you can notice something is odd with the decoded string it has double quotes which means that the phrase is the literal as it is
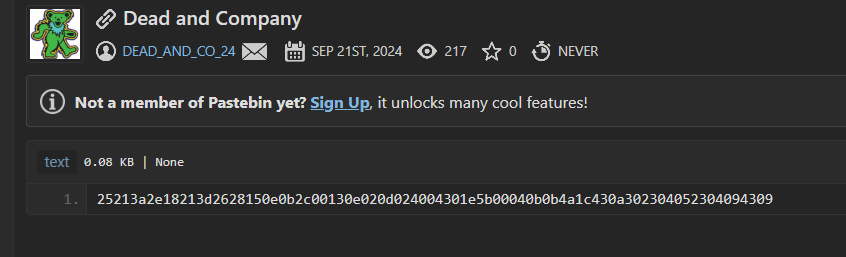
25213a2e18213d2628150e0b2c00130e020d024004301e5b00040b0b4a1c430a302304052304094309
trying hex and other decodings nothing works and I got stuck here, here we have a new aspect that recently joined which is the Pastebin profile itself (it’s the last possible hope also) I got this public paste
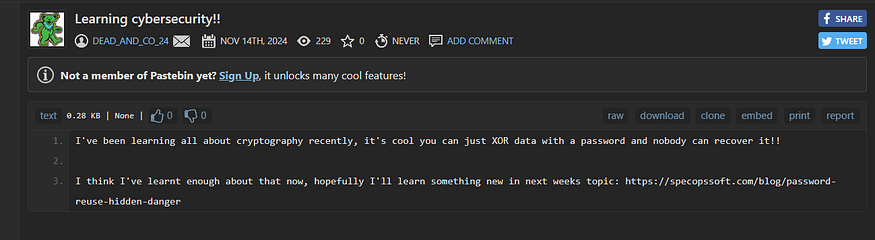
I got stuck here, going with the provided link and sealed
but it was just a hint to XOR the secret paste we have to get the flag 😐
That’s it for today's challenges see you next ones If you have any questions, You can reach me through my social accounts: Twitter(X) | Linkedin | Github |Facebook
Last updated