PicoCTF 2024 General Skills Challenges
PreviousPicoCTF 2024 Web Exploitation ChallengesNextPicoCTF 2021 Web Exploitation Challenges Walkthrough
Last updated
Free Palestine, Free Gaza
Hello and welcome again, I’m Ahmed Reda (0xHunterr) and this is a walkthrough for some of the Web Exploitation & General Skills Challenges of PicoCTF 2024 Live

Challenge Link
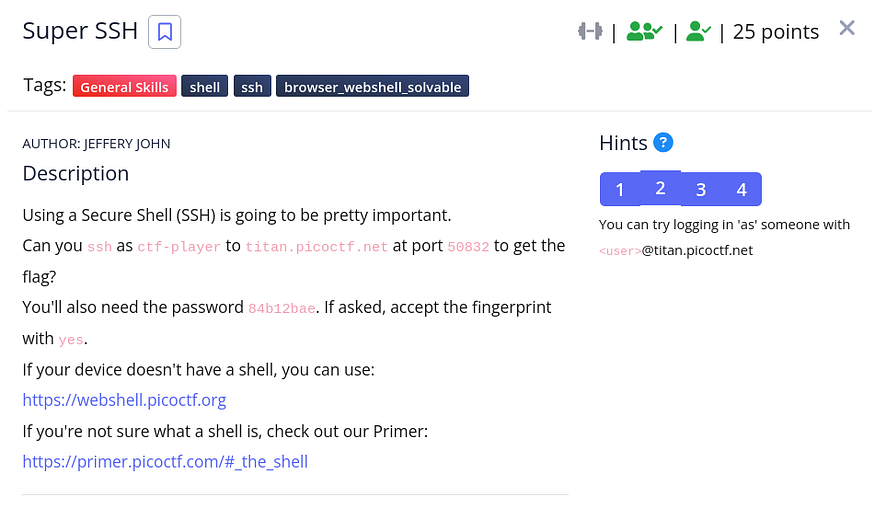
It’s just about connecting through SSH, we can solve it using the following command: ssh -p 50832 [ctf-player@titan.picoctf.net](mailto:ctf-player@titan.picoctf.net)
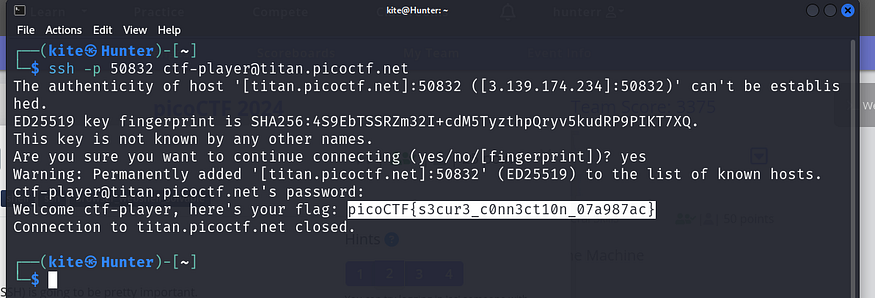
the flag : picoCTF{s3cur3_c0nn3ct10n_07a987ac}
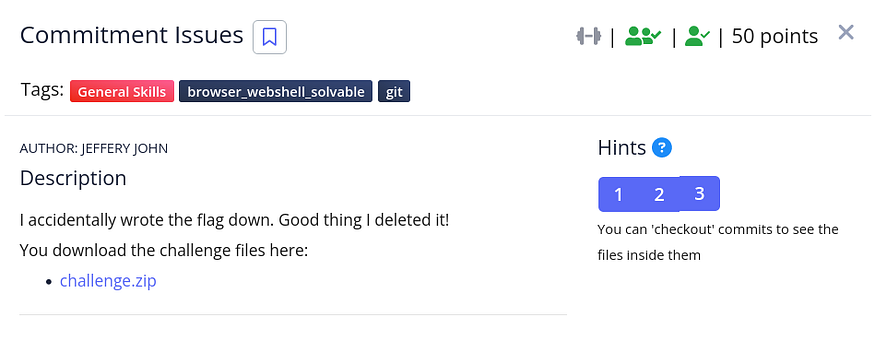
provided with a Zipped file to download, after unzipping it I got the following unzip challenge.zip
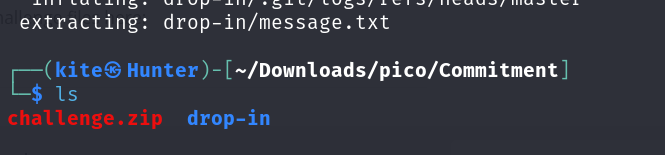
the challenge folder contains a message.txt file
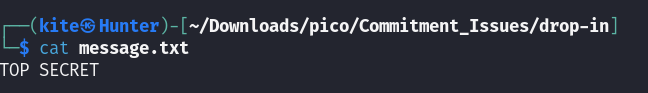
the hints of the challenge are talking about git commits so checked the git log
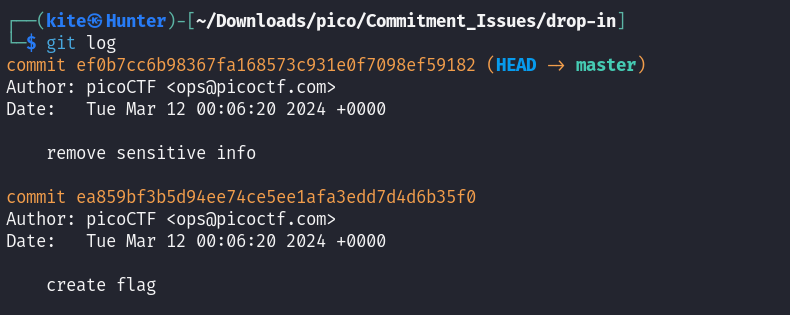
we can see that the first commit has the message that says “remove sensitive info“ so that’s exactly what we are looking for, let’s revert that commit
git checkout ef0b7cc6b98367fa168573c931e0f7098ef59182
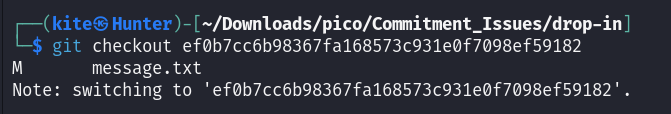
now let’s read the file before deleting the sensitive info
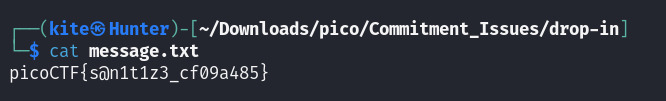
the flag: picoCTF{s@n1t1z3_cf09a485}
so after downloading the file and unzipping it we got :
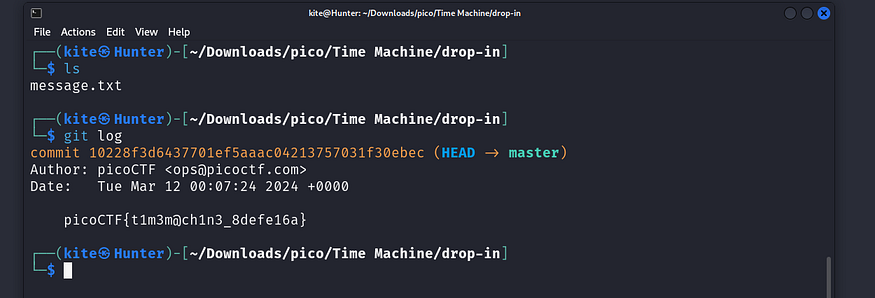
wow, this was pretty fast☹ ..anyway
the flag: picoCTF{t1m3m@ch1n3_8defe16a}
that’s it for this CTF see you in the future Inshaa Allah, Pray for me 🙏
If you have any questions, You can reach me through my social accounts:
Twitter(X): https://twitter.com/HunterXReda Linkedin: https://www.linkedin.com/ Facebook: https://www.facebook.com/profile.php?id=100012814653588

“Hide the Pain”
Last updated